How to Configure MacOS to Use Active Directory LDAP for UNIX users/groups | Why Is The Internet Broken?

Prerequisiti per l'utilizzo di Microsoft Active Directory autogestito - Amazon FSx per Windows File Server
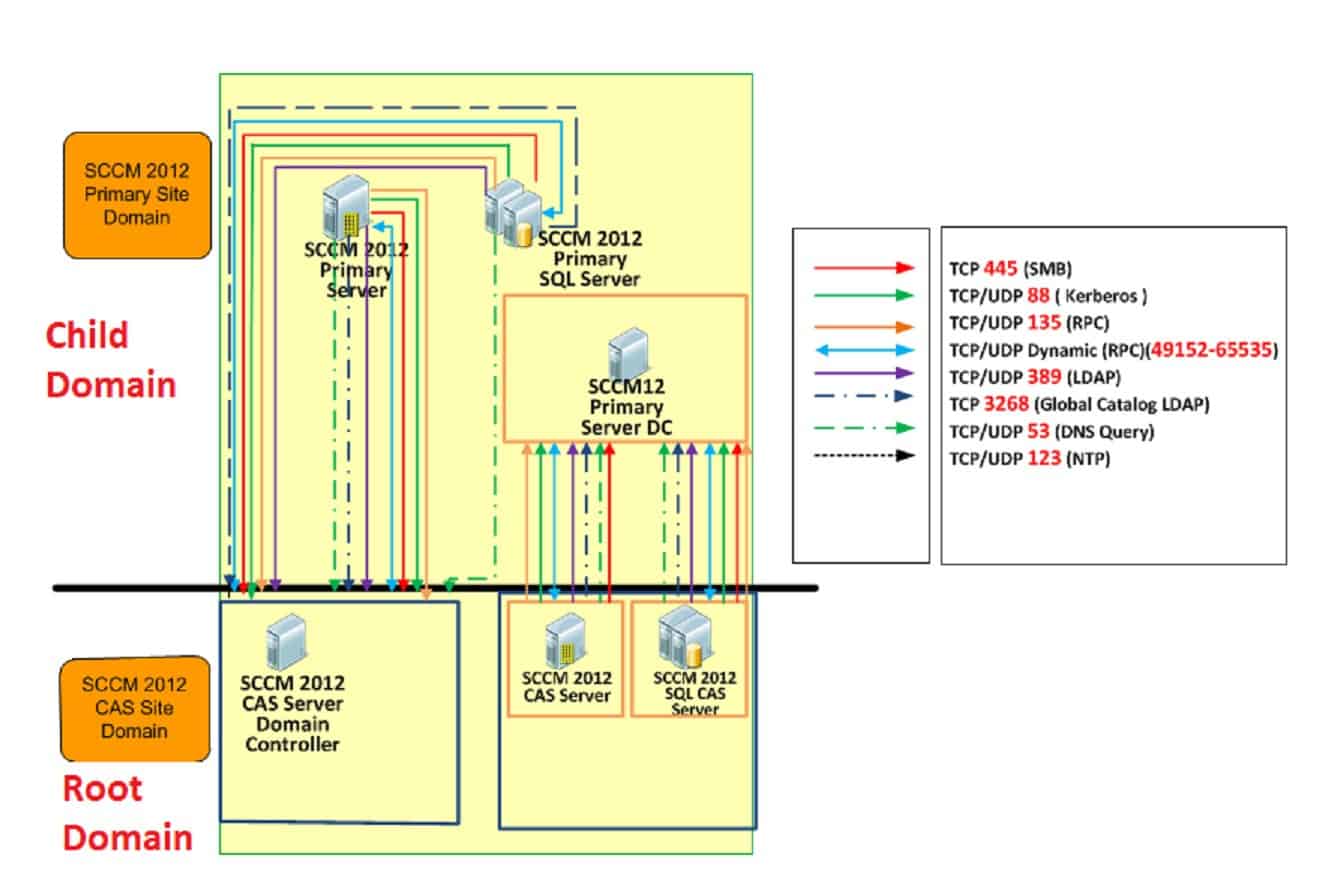
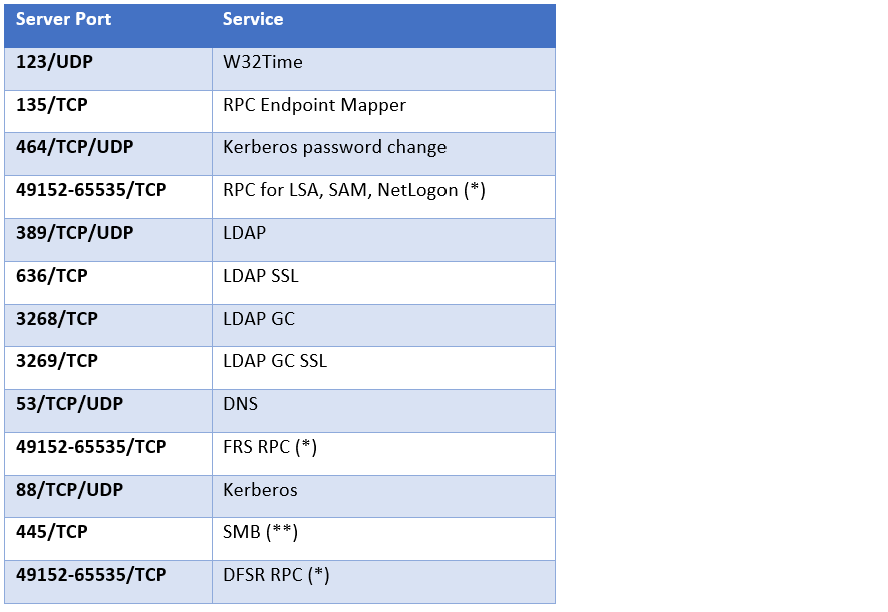
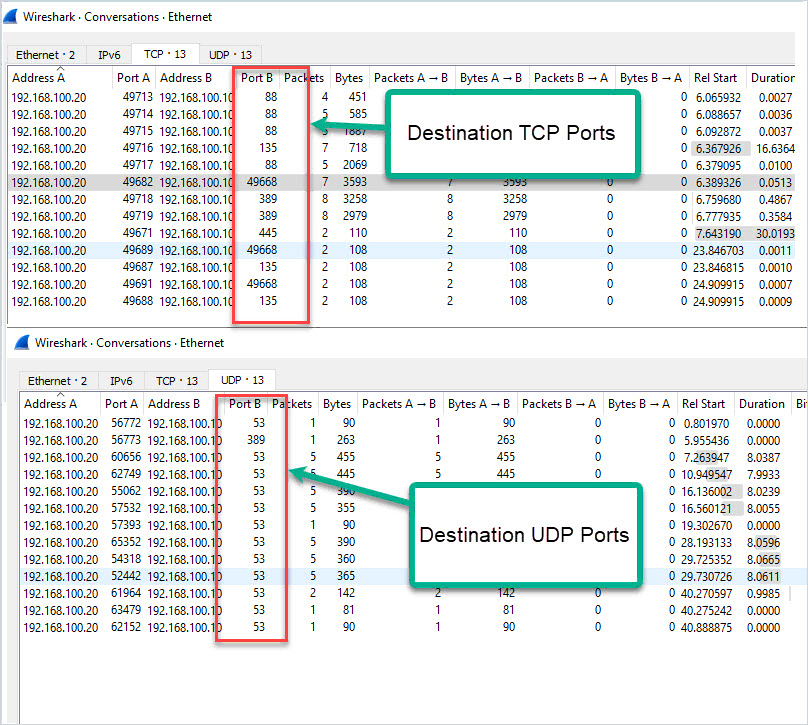
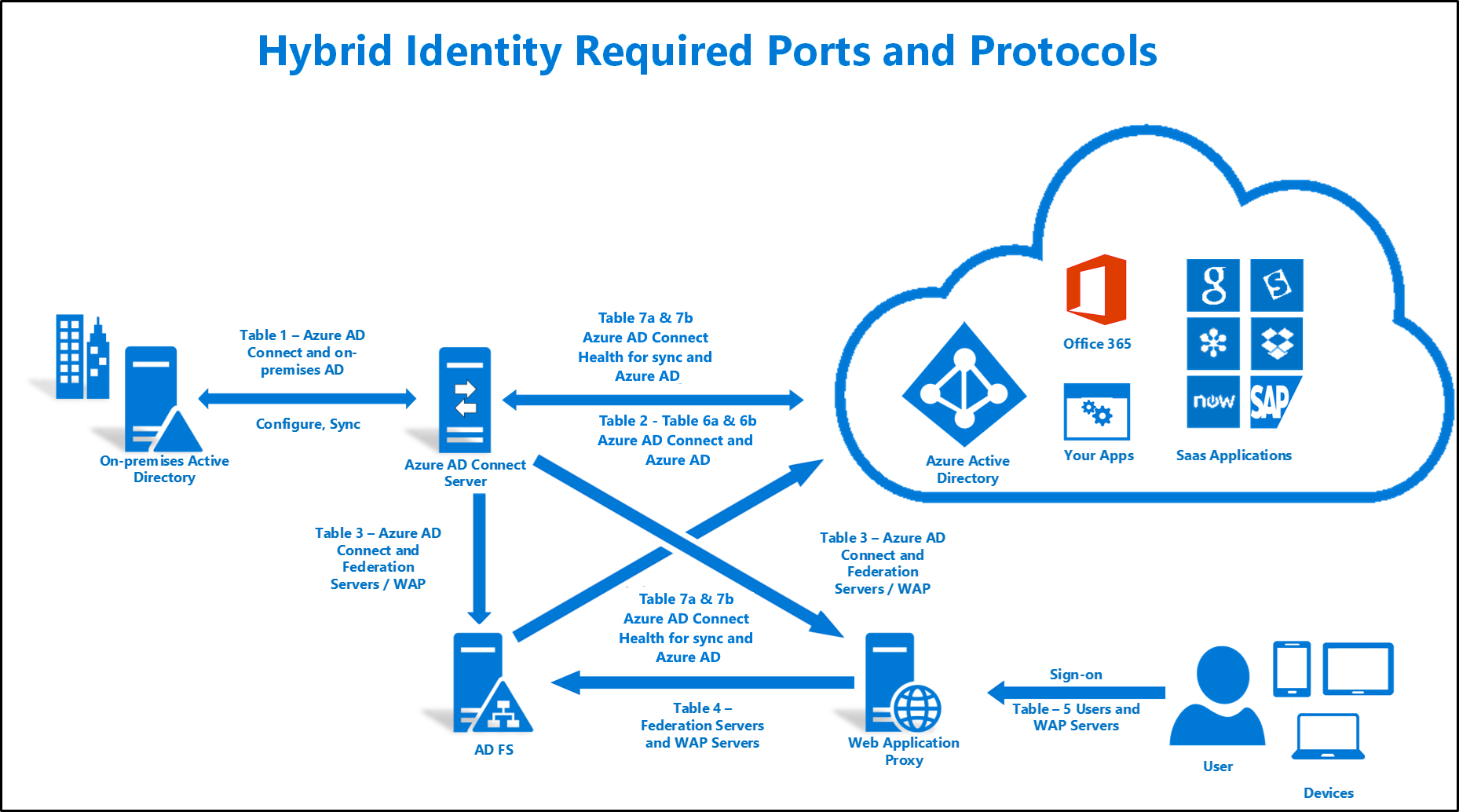
SCCM Firewall Ports Details Direction With DC Other Servers | Configuration Manager | Bi-direction HTMD Blog
LDAP integration using global catalog port 3268 cannot retrieve user or person object class (table) - Discussion - BMC Community

active directory - Can not promote server to domain controller because required ports are already in use - Server Fault

Active Directory Account Data Collection fails to retrieve Active Directory attributes when connecti... - RSA Community - 5466
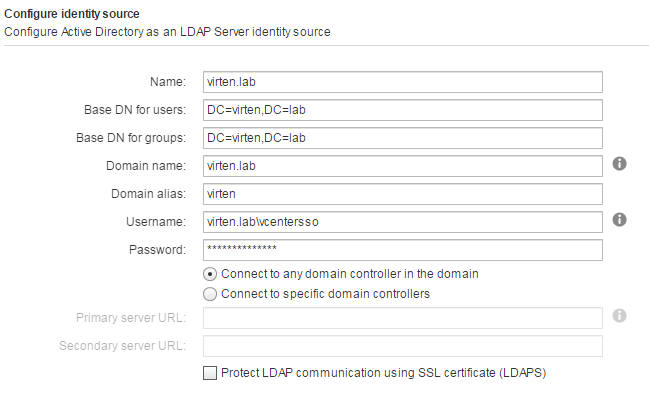
LDAP users cannot log into NSX-T UI or are automatically logged out after 5 minutes when AD has subdomains (83603) | VMware KB

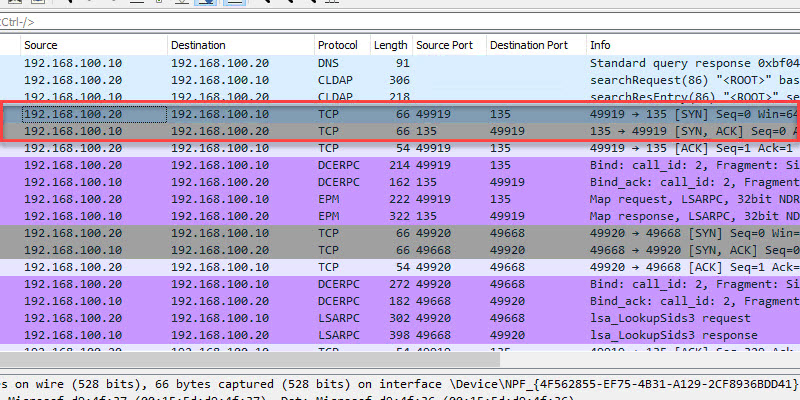
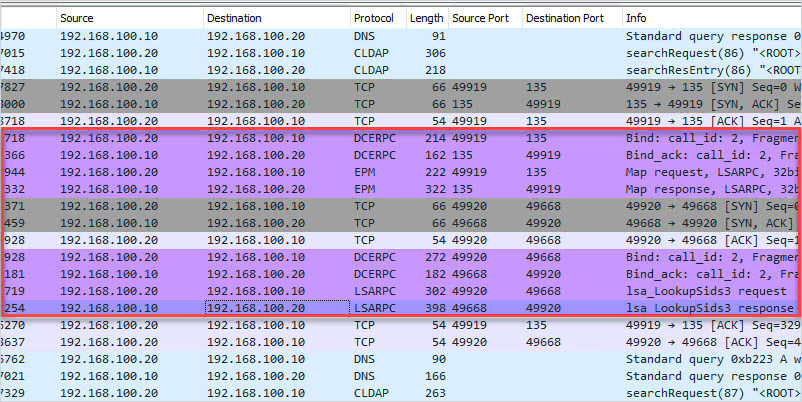
Active Directory: What do CTF environments teach us about attacking Domain Controllers? — Introduction | by Piotr Stachyra | Medium